User role controlled by request parameter
Introduction
Portswigger
Category: Access control vulnerabilities
Write-up date: 10/06/2025
Question: This lab has an admin panel at /admin, which identifies administrators using a forgeable cookie.
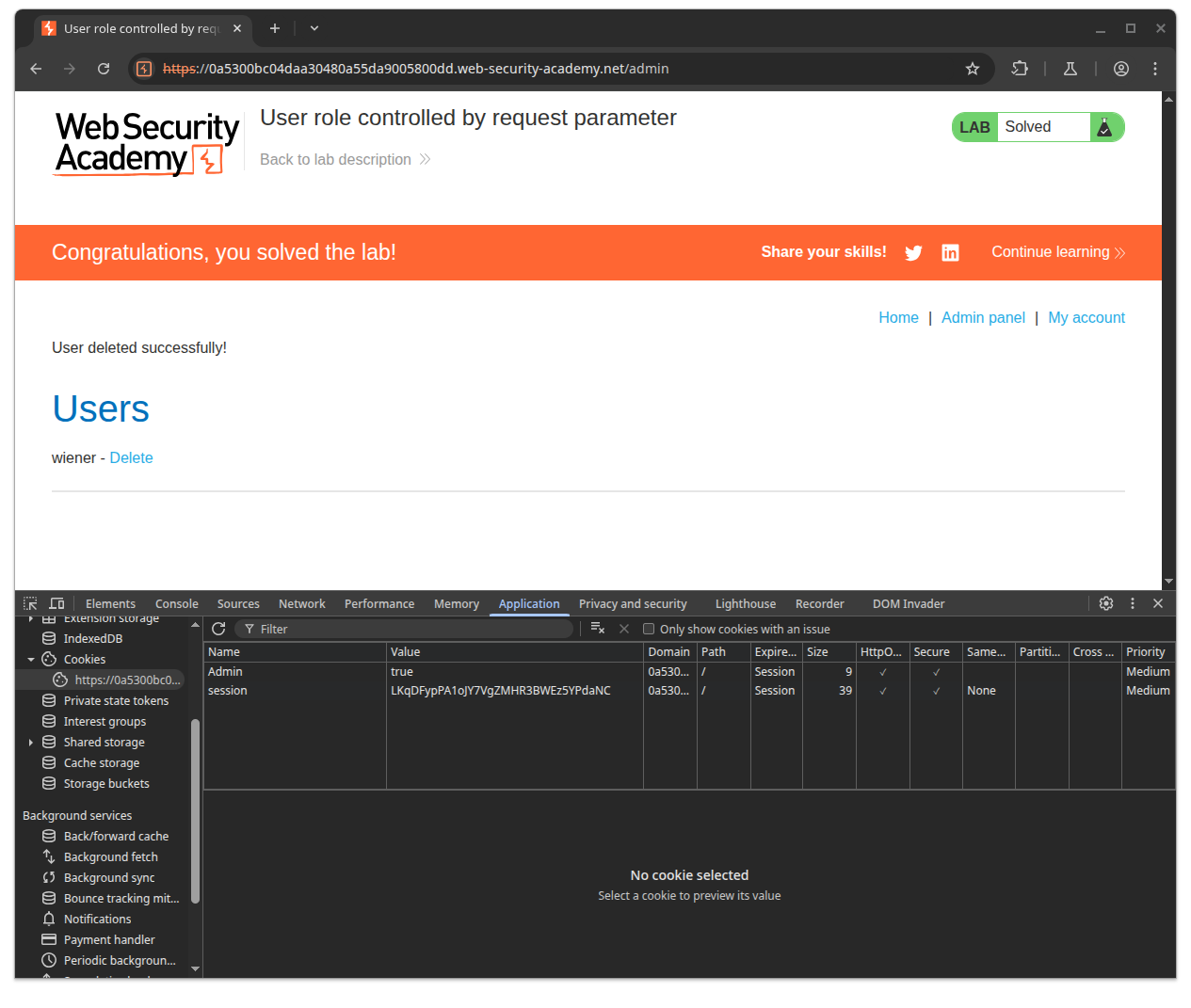
Solve the lab by accessing the admin panel and using it to delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
Point: APPRENTICE
Recon
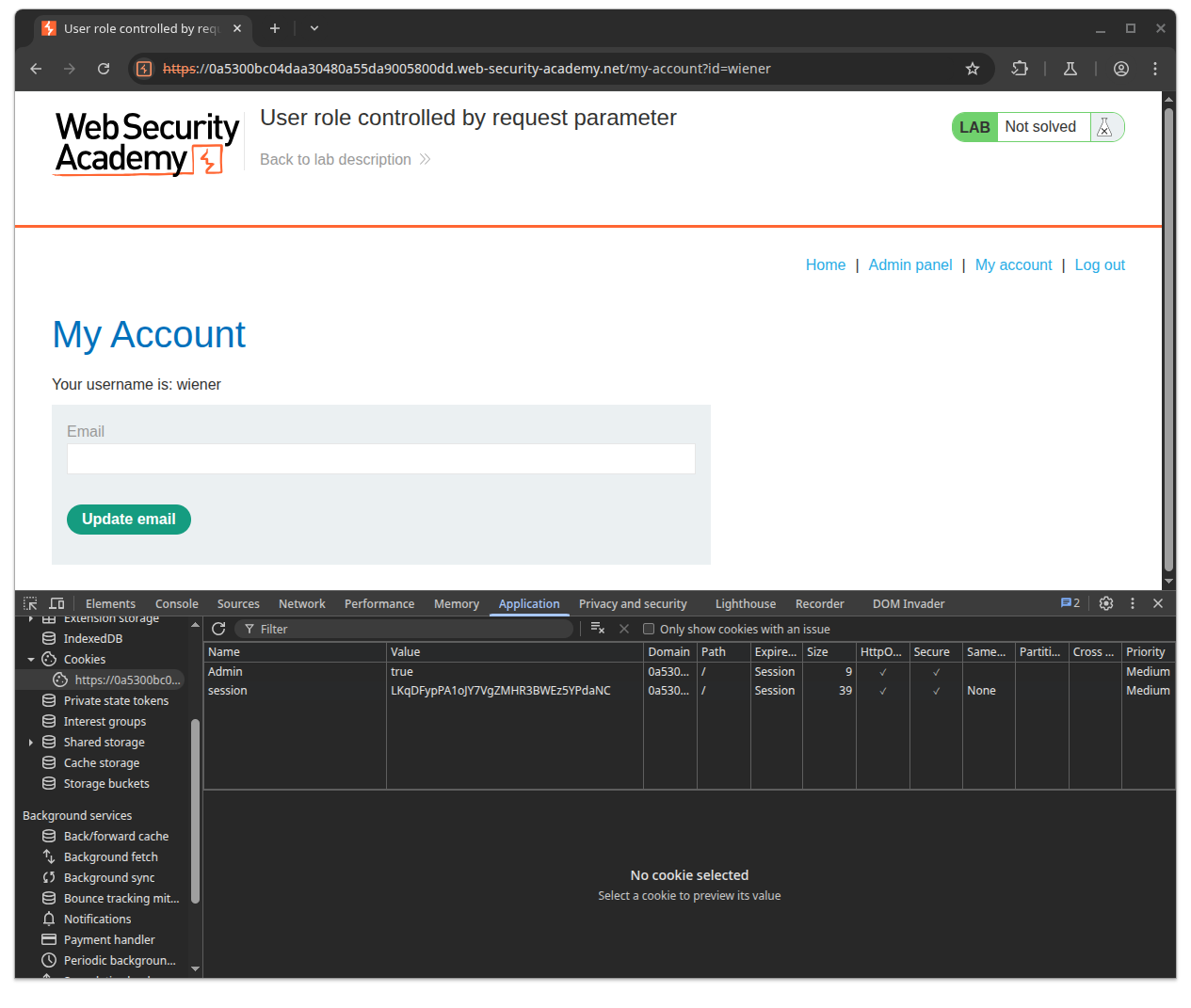
Logged into wiener account, the url redirect us to /my-account?id=wiener endpoint with the cookies
HTTP/2 302 Found
Location: /my-account?id=wiener
Set-Cookie: Admin=false; Secure; HttpOnly
Set-Cookie: session=redacted; Secure; HttpOnly; SameSite=None
X-Frame-Options: SAMEORIGIN
Content-Length: 0
Exploit
So the lab decide if you are admin or not through unprotected Admin cookies, which user has completely full access to
override without the server know it has been compromise or not.
Simply change the Admin to true, reload the page, and you have the admin permission.
Access the admin panel then delete user carlos to complete the lab.