User role controlled by request parameter
Introduction
Portswigger
Category: Access control vulnerabilities
Write-up date: 10/06/2025
Question: This lab has user account page that contains the current user's existing password, prefilled in a masked input.
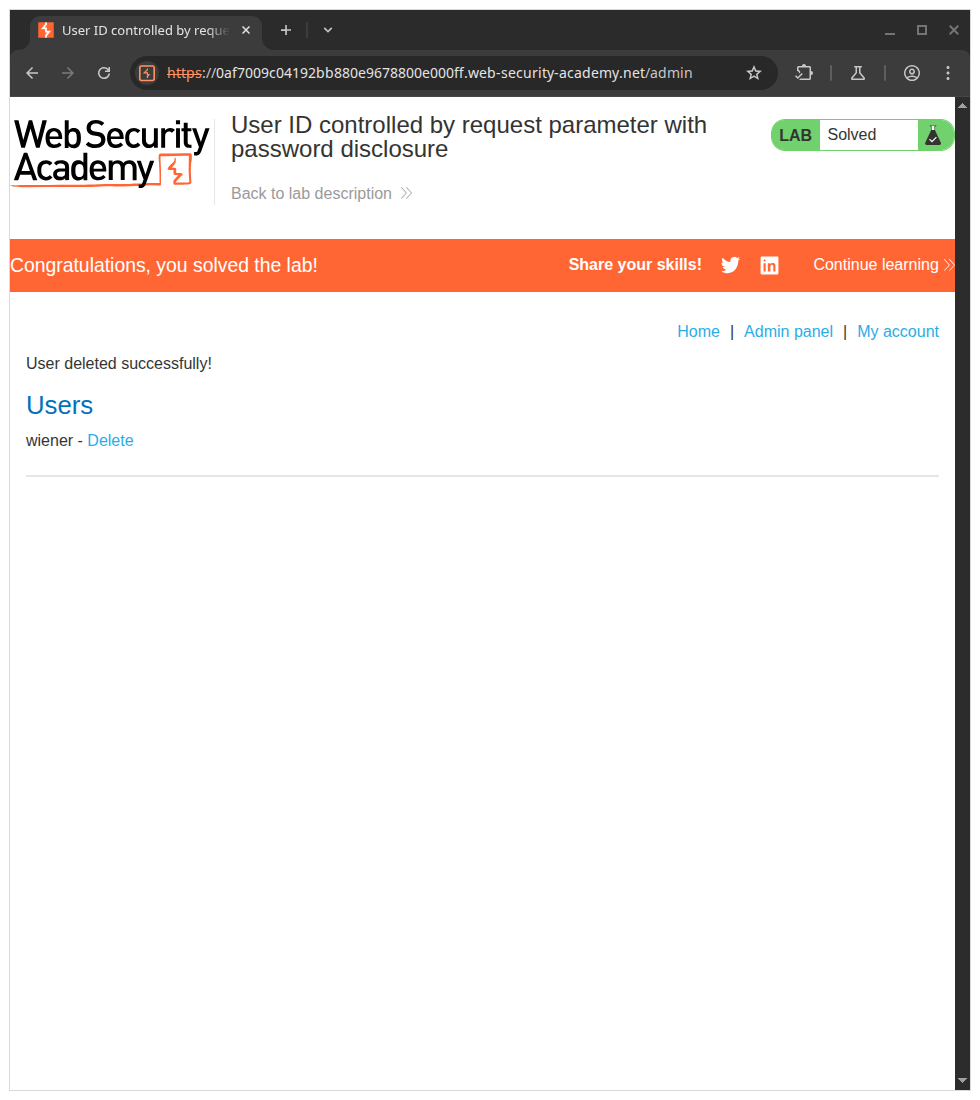
To solve the lab, retrieve the administrator's password, then use it to delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
Point: APPRENTICE
Recon
Logged into wiener account, the url redirect us to /my-account?id=wiener.
At the url param, we can confirm that id param correspond to each user. In that panel have a function to change the
password and the password send to client is plaintext password. Meaning you can use that password to log in to that
account.
Exploit
Normally user shouldn't have the permission to access other information. But when logic error happened in the server, you can easily access other profile information and steal their information. Also, when saving password to database, you shouldn't use plaintext password, because when data leaks happened, the attacker will see the password allow deeper penetration into the system if you use the same password.
Change id to administrator(/my-account?id=administrator) reveal administrator password.
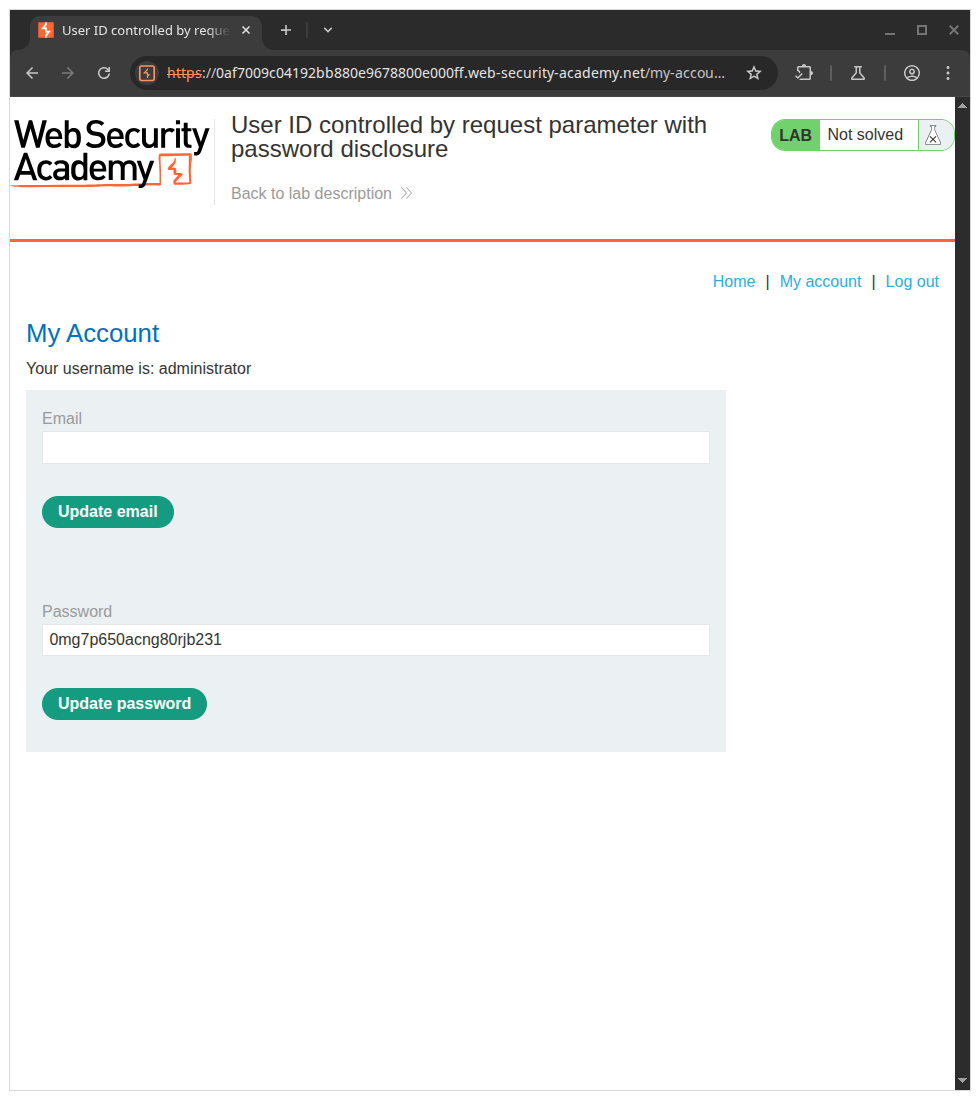
Using password above, login into administrator account to access admin panel then delete carlos to complete