Unprotected admin functionality with unpredictable URL
Introduction
Portswigger
Category: Access control vulnerabilities
Write-up date: 10/06/2025
Question: This lab has an unprotected admin panel. It's located at an unpredictable location, but the location is disclosed somewhere in the application.
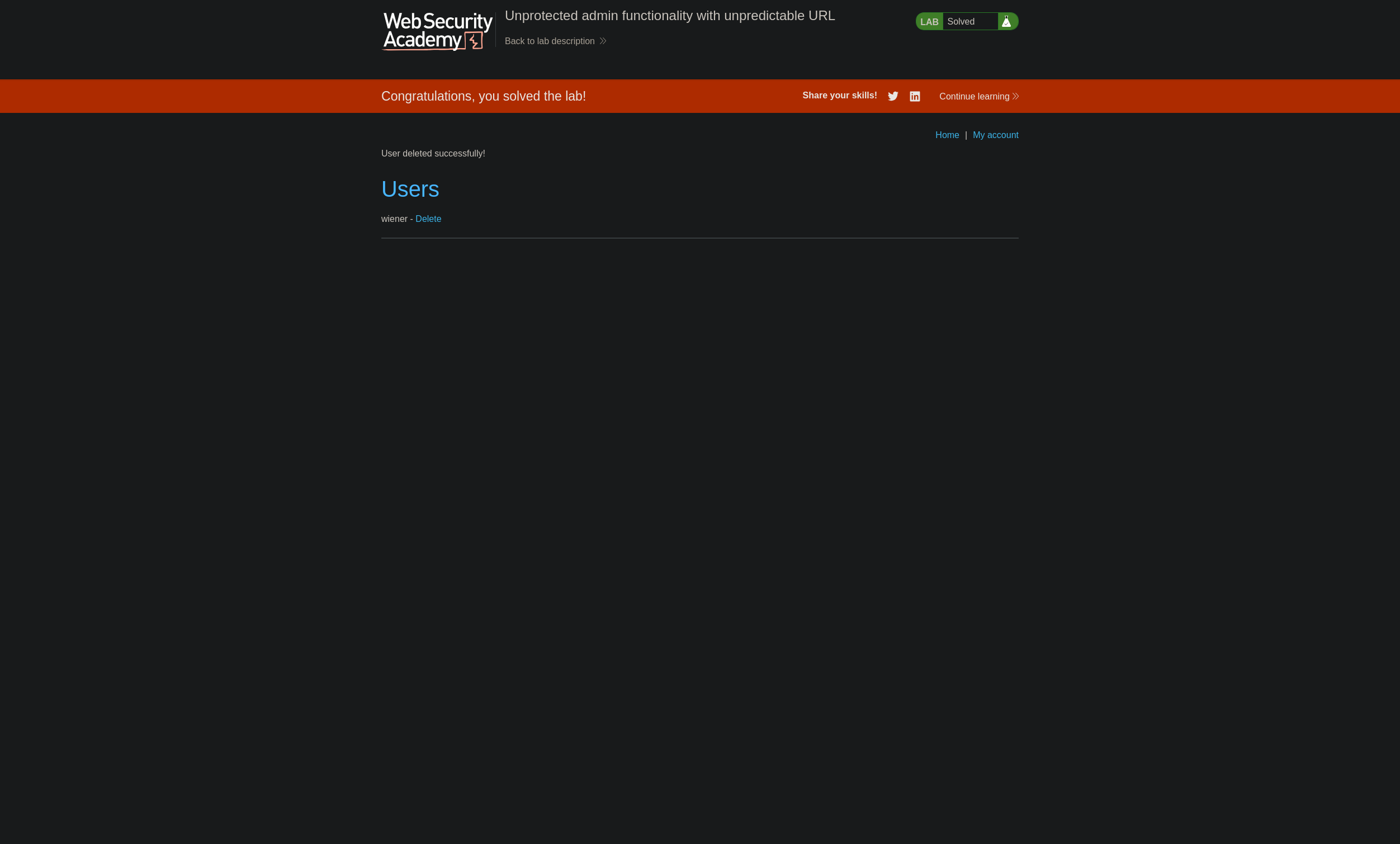
Solve the lab by accessing the admin panel, and using it to delete the user carlos.
Point: APPRENTICE
Recon
View the source code of index page, we have some strange looking javascript
var isAdmin = false;
if (isAdmin) {
var topLinksTag = document.getElementsByClassName("top-links")[0];
var adminPanelTag = document.createElement('a');
adminPanelTag.setAttribute('href', '/admin-4h8xzu');
adminPanelTag.innerText = 'Admin panel';
topLinksTag.append(adminPanelTag);
var pTag = document.createElement('p');
pTag.innerText = '|';
topLinksTag.appendChild(pTag);
}
The code is checking if the user isAdmin or not. If the user admin, create new a tag that have text Admin panel and
point to url /admin-4h8xzu
Exploit
Access url /admin-4h8xzu and like the previous lab, delete carlos user.