My Aquarium
Introduction
DawgCTF
Category: Fwn (Web)
Write-up date: 24/04/2025
Question: I have this website with some of my favorite sea animal images and facts. I have a secret document containing an my favorite animal, can you find it?
Point: 200
Recon
When access the page, first we can see the page have 3 function.
- See Sea Animals
- Sea Animals Facts
- Take this quiz to find out what sea animals you are!
Visits See Sea Animals, its just a gallery of fish image so we can safely ignore it for now.

Continue to Sea Animals Facts, the button redirect us to another
url https://onlineaquarium.blob.core.windows.net/aquarium/resources/sea-animal-facts.txt. The domain *
.blob.core.windows.net is a domain for Azure Cloud services. Azure Blob have some misconfiguration that can lead to
exposed data access, reveal file structure for anonymous user.
Last one, visits Take this quiz to find out what sea animals you are! function, the page show a form of some kind.
When check the source code of this page, we can clearly see that there no flag hidden inside the page. Submit the form,
the page doesn't reload, nor send any network request. So we can also ignore this function.
So in the recon phase, we left with the page that we can exploit is https://onlineaquarium.blob.core.windows.net/aquarium/resources/sea-animal-facts.txt
Exploit
We can access and interact the Azure blob via multiple way: REST API, Azure CLI, Azure Portal. For the rest of this write-ups, I choose Azure Storage Explorer because it fairly lightweight and it has GUI 😔.
Because we want to check out the Azure Blob, we select Connect to Azure resource
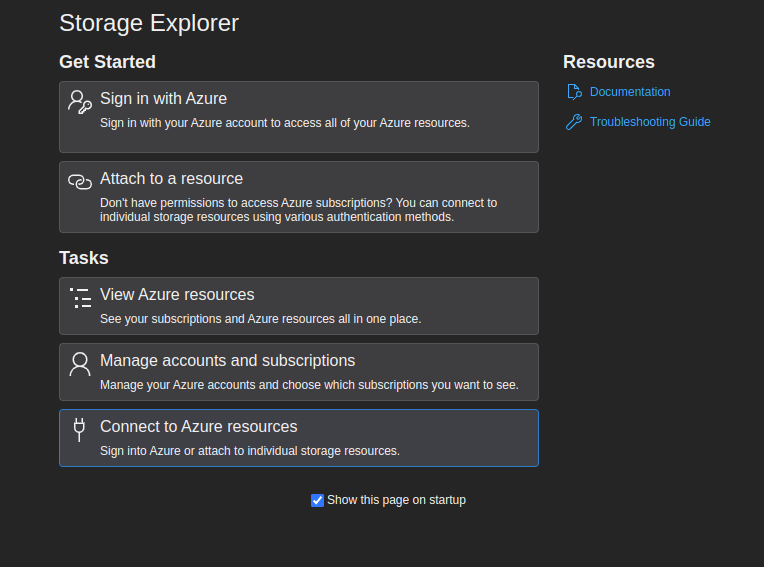
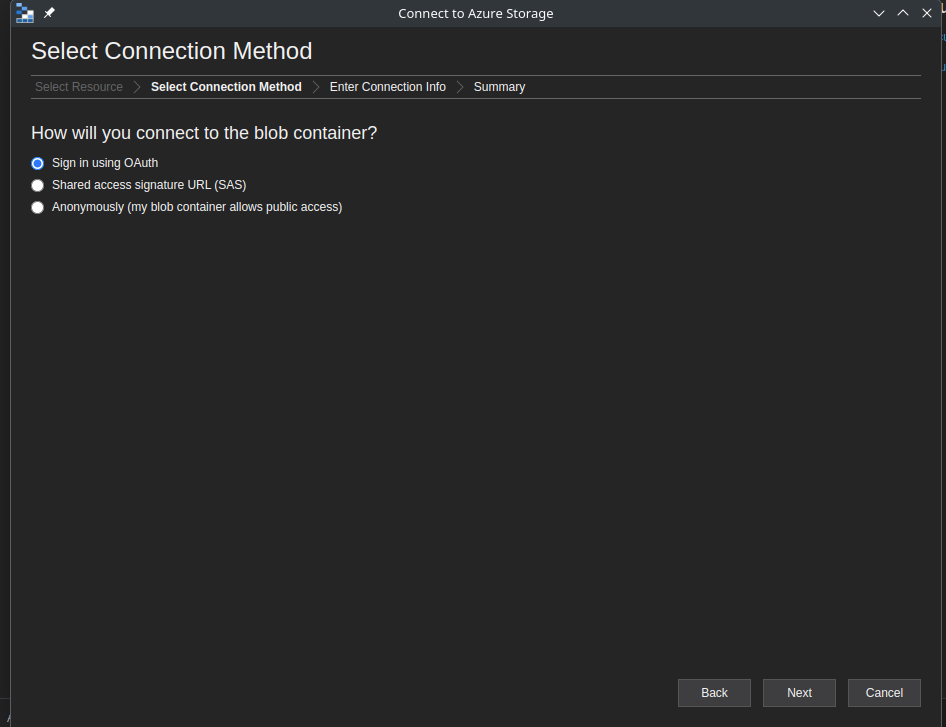
Then the screen popup ask what resource we want to connect to, because the file located in *.blob domain so we choose blob container or directory.
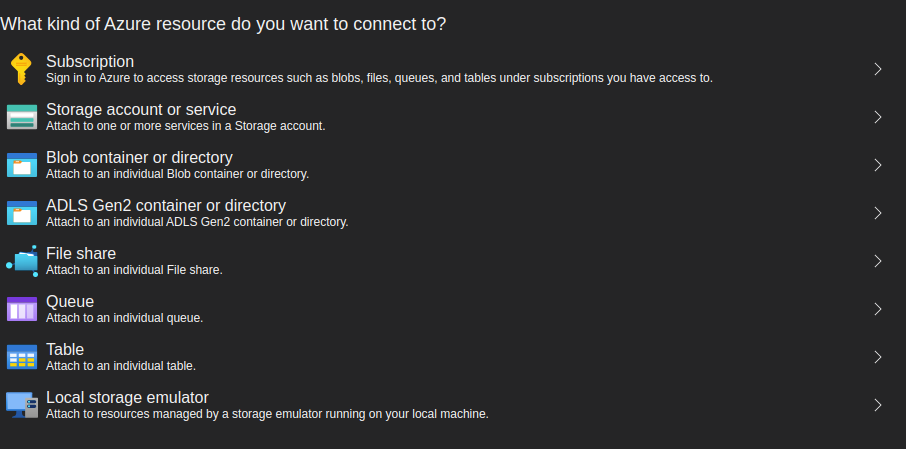
Because we can access the blob resource publicly (Eg: sea-animal-facts.txt), we can simply choose Anonymously to access the rest of the resource.
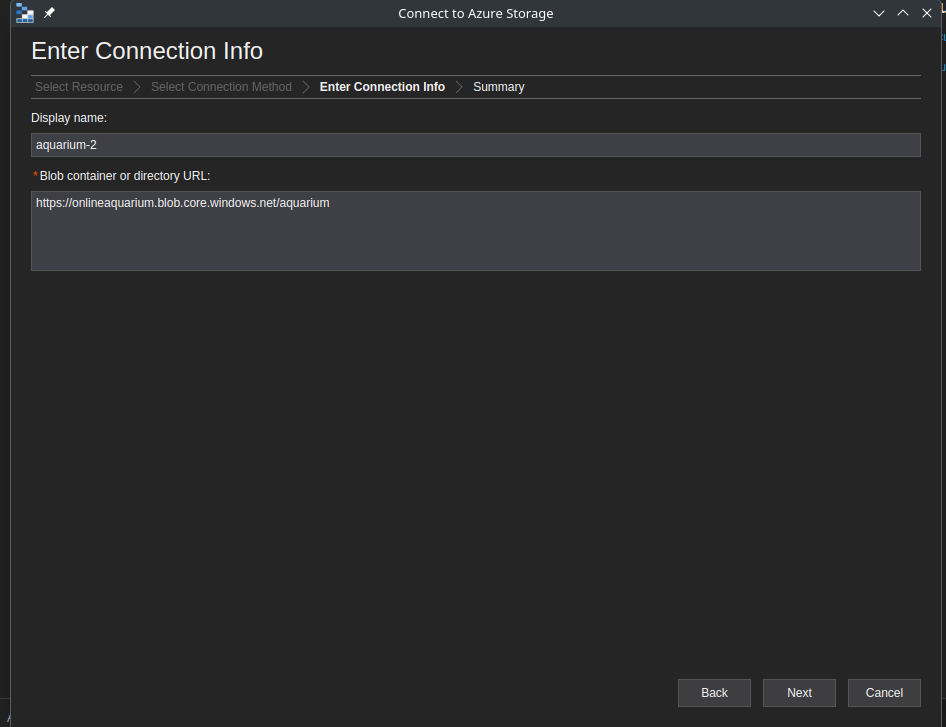
Next, in the blob container, paste the url of the blob contain see-animal-fact.txt file into the Blob container url.
Exploring the resource directory give us this:
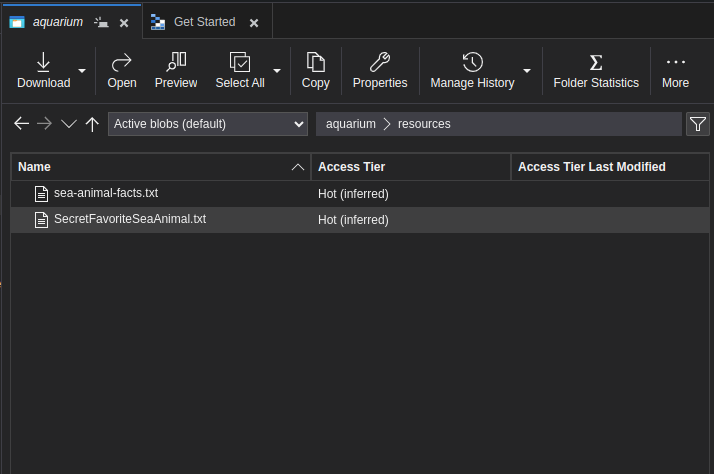
Open SecretFavoriteSeeAnimals.txt revals the flag
FLAG: DawgCTF{Bl0b_F15h_4re_S1lly}